How are you using and storing sensitive usernames and passwords in Flow? We use usernames and passwords for so many different actions in Flow. One main use is in a HTTP action.
In scenarios like this, where do you store these usernames and passwords? This post will show how to use Azure Key Vault action to get a secret, which can be passed to any action securely using Secure Inputs and Outputs.
Prerequisites
- Azure Subscription
- Azure Key Vault setup
- Key Vault Permissions set to Get and List Via Access Policy
- Key Vault Secret created
- Premium License for Power Automate
Steps
Okay, now that we have the above prerequisites ready, lets get the Flow created
First we want to search for ‘Azure Key Vault‘ when adding a new action in our Flow. We will use the ‘Get Secret‘ action
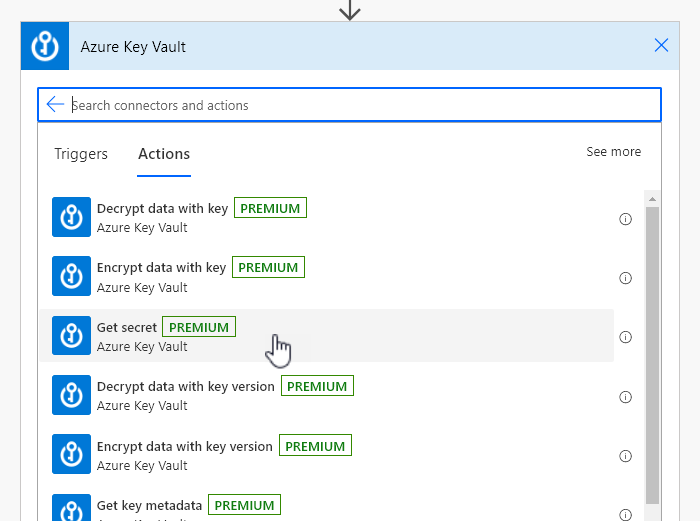
When creating the connection, you will be asked for the Key Vault name. This is the display name that is in Azure.
Next, we add the name of the Secret we want to get. I also Initialize a variable to store the Secret in for easier reference later in my Flow
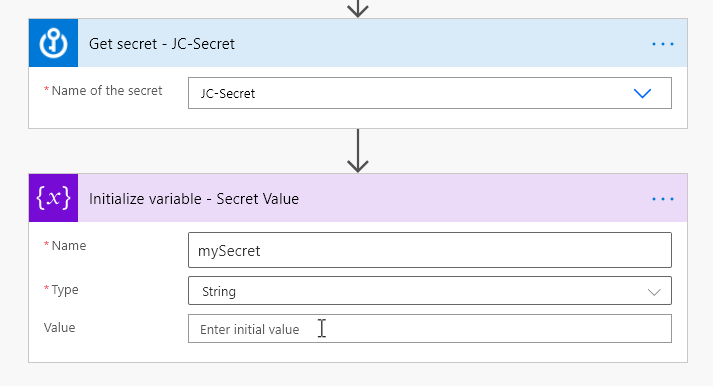
Inside the Variable, I select the Dynamic content Value.
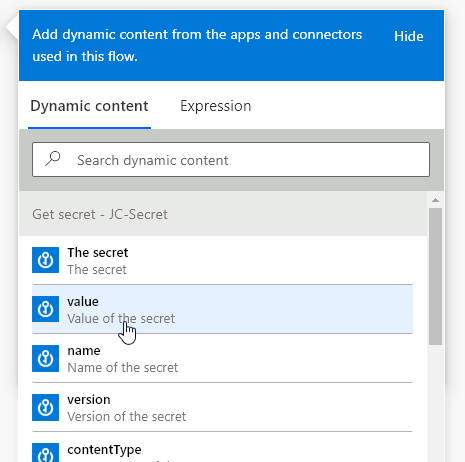
Now, I run the Flow…
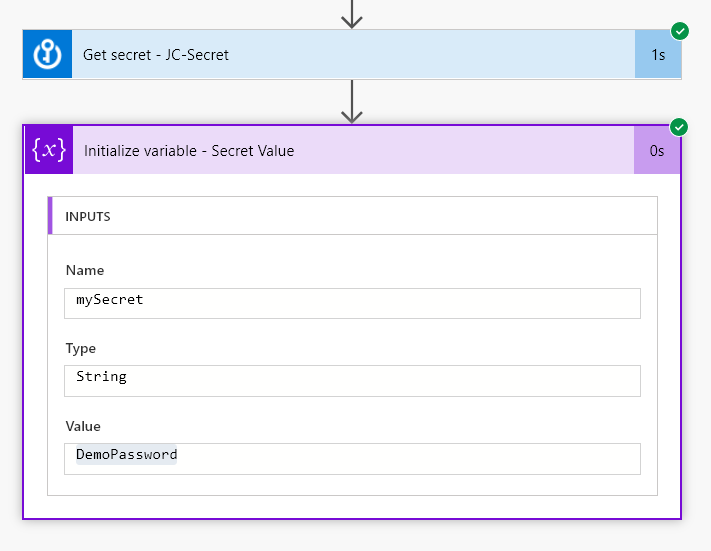
Oh Uh, that doesn’t look good.. Our Secret is wide open and visible in the run history. We can easily fix this.
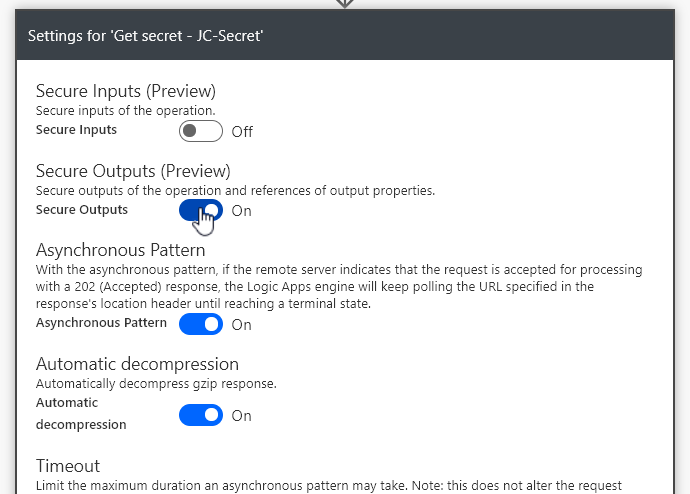
On the Get secret action we want to enable Secure Outputs
We do this by:
Clicking the 3 dots on the Get Secret action,
Go into settings,
Enable Secure Outputs.
Click Done
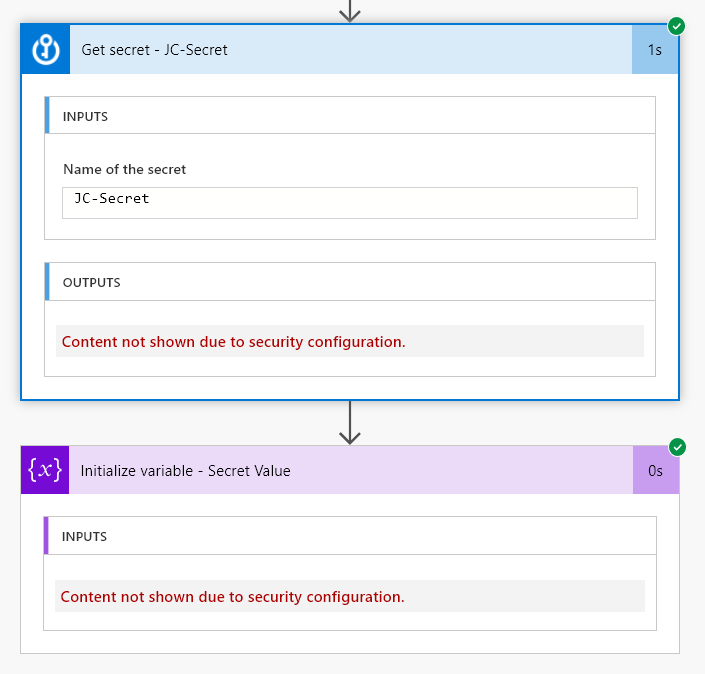
Now when we run then Flow, the Secret value will be hidden from the run history, in all actions.
Thanks for reading!!
If you have any questions, please reach out.
![Flow Alt Delete – Josh Cook [Microsoft MVP]](https://flowaltdeleteca.files.wordpress.com/2020/04/cropped-img_0521.jpg)


What are the minimum roles for a least priveleged user to retrieve a secret from the vault? “Secret Permissions:Get” alone is not enough.
LikeLike
Answer: “Get” and “List”
LikeLike