Virus Total in Power Automate. Now we can scan links or files and generate a report, right in Power Automate. Some examples may include: Links or files from Emails, Teams, Etc.
What is Virus Total
Virus Total is a free and powerful tool to scan Files, and Links. Virus Total uses the Hash of the File/URL and checks some of the most popular antivirus systems to generate a report. https://www.virustotal.com/
Prerequisites
This is a Premium connector
Note: These actions of the time of this blog, are in Preview.
Virus total has two types of API
Free (Public):
– The Public API is limited to 4 requests per minute and 1K requests per day.
– The Public API must not be used in commercial products or services.
– The Public API must not be used in business workflows that do not contribute new files.
Paid (Premium):
– The Premium API does not have request rate or daily allowance limitations, limits are governed by your licensed service step.
– The Premium API returns more threat data and exposes more endpoints and functionality.
– The Premium API is governed by an SLA that guarantees readiness of data.
Keep the above information in mind when using the API
To use the Virus Total connector, you must sign up on their site and get a token. To get the token, follow these steps:
First head over to https://www.virustotal.com/ and sign up for free
Next you will have to confirm your email address
Now once you can login to your account, you want to click your person logo in the top right, and select API key

Now copy the API key that you are given. That is it! Now you can use that Key to create a connection with the Virus Total Connector is Power Automate
Connection Setup
First, we make a connection to the Virus Total API.
In your Flow, add a new action, search for Virus Total.
Virus Total has a couple Actions here that are very powerful.
We will be using ‘Analyse an URL’ action for this demo.

All that is needed to create the connection is your API key from the prerequisites.
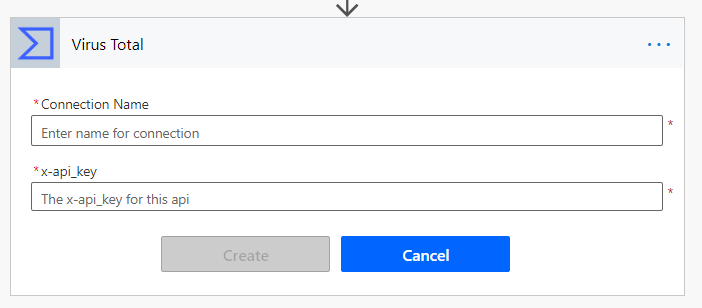
Connection name can be anything you want, for this demo I chose VirusTotalDemo
Now that we have the connection established we can build the Logic for analyzing a URL.
Building the Flow
I will be using a Button trigger, and a Variable to store the URL I want to analyze but I will go through some use cases at the end of this blog of how this can be implemented.
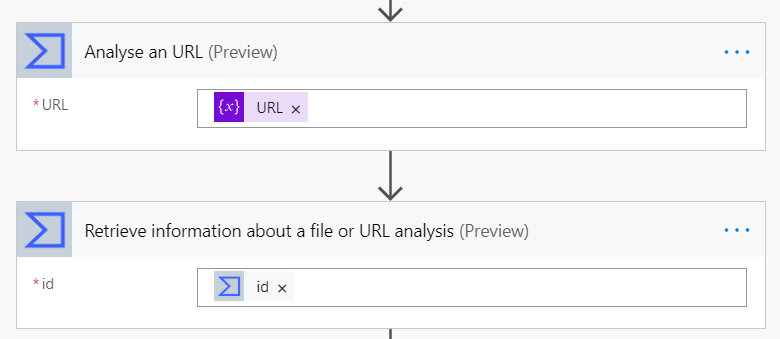
There are two main actions in the Virus Total connector I will be using:
– Analyse an URL
– Retrieve information about a file or URL analysis
I am using a string variable to store the URL.
Now we use the Virus total action called: Analyse an URL. This action only needs one input, the URL we want to analyse. This action outputs the ‘id’ for the analysis. We can use this ‘id’ in our next action.
Now we add the second Virus Total action called: Retrieve information about a file or URL analysis. This action wants the ‘id’ from the first step.
From here we get a bunch of cool dynamic content for the stats of this URL.. But for this demo, I will use the ‘stats’ dynamic content, this is a JSON object so I will add a Parse JSON action.
To get the schema, you can either copy my schema, or use {} inside your schema, and run the flow, than copy the outputs to ‘Generate from sample’

My schema is:
{
"type": "object",
"properties": {
"harmless": {
"type": "integer"
},
"malicious": {
"type": "integer"
},
"suspicious": {
"type": "integer"
},
"timeout": {
"type": "integer"
},
"undetected": {
"type": "integer"
}
}
}From parsing the ‘stats’ object, I am able to check if the URL has any harmless, malicious, suspicious, or undetected reports. This information can be very useful.
Now I can add a If condition and control what kind of sites I want to classify as harmful or malicious. Here is my condition:

If URL has 3 or more report engines pick up the URL as Malicious, OR if the report has less than 50 harmless reports. That I am classifying this URL as BAD
Use Cases / Conclusion
I have only scratched the surface with Virus Total in this blog. I am sure lots of people can find a great use out of this. A great example of how this can be used:
Have users send files or URLS, which can get analyzed, to help with cyber security. Could trigger by:
– Flow bot in Teams
– Have a flow monitor a certain email, which can parse the body for URLS, and check for attachments
Thanks for reading!
![Flow Alt Delete – Josh Cook [Microsoft MVP]](https://flowaltdeleteca.files.wordpress.com/2020/04/cropped-img_0521.jpg)

